In the era of digitalization, one of the most vexing realities is that it is becoming increasingly challenging for businesses to manage their cybersecurity risk. The future appears to be even gloomier as, on average, 130 security breaches were reported by businesses in 2021. (Purplesec.us) This is where cybersecurity came in just like a shot in the dark.
Cybersecurity risk management is all about essential components of any organization's strategy to protect itself from cyber threats. Cybersecurity risk management involves identifying, assessing, and prioritizing risks, and developing strategies to mitigate those risks. In this blog, we will discuss best practices for cybersecurity risk management to help organizations better protect themselves from cyber threats.
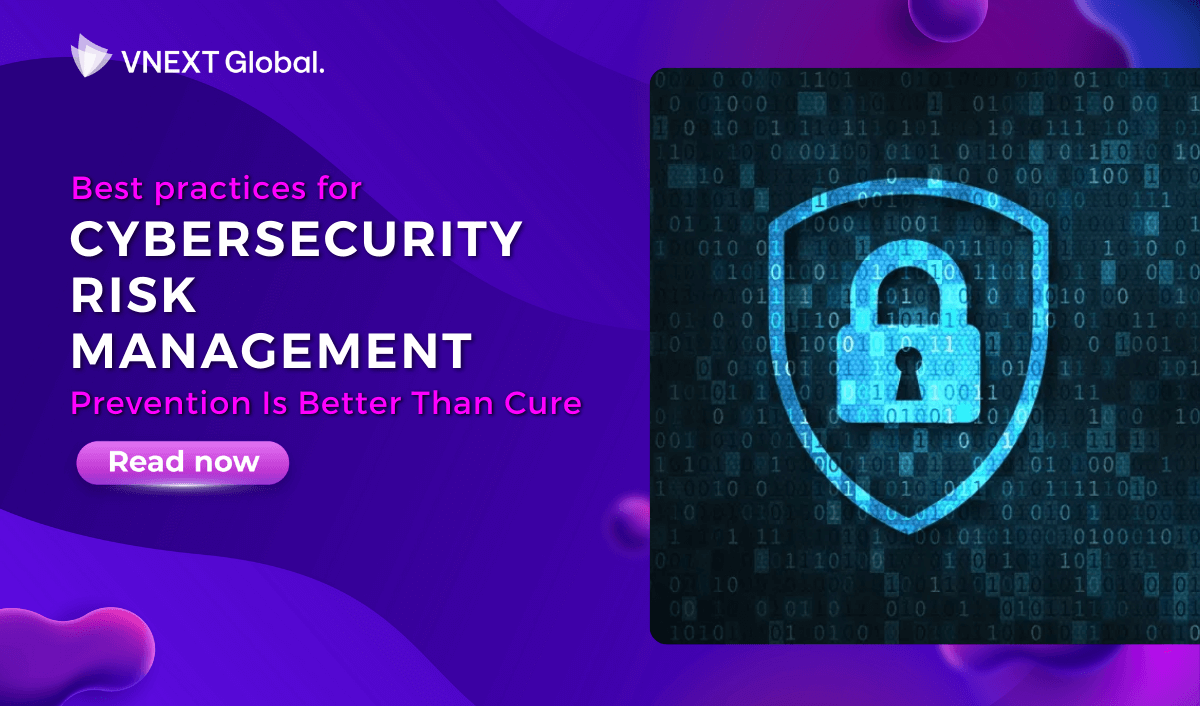
Best Practices for Cybersecurity Risk Management - Prevention Is Better Than Cure
1. Definition of Cybersecurity Risk Management
Management of cybersecurity risks entails determining which threats pose the greatest danger and then formulating plans to counteract them. The purpose of managing cybersecurity risks is to safeguard a company's sensitive data and infrastructure from compromise. Security controls, policies, procedures, and technologies are all used in cyber risk management to mitigate the effects of cyber attacks.

2. Risk Identification
Cybersecurity risk management begins with the identification of threats. The first step is to catalog the dangers, weaknesses, and resources that exist in the system.
A. Identification of Threats
Threats are potential events or actions that can cause harm to an organization's information or information systems. Some common threats include malware, phishing attacks, denial of service attacks, and insider threats. According to a report by the Ponemon Institute, the average cost of a cyber attack in 2021 was $4.24 million. This highlights the importance of identifying threats and developing strategies to mitigate those threats.
B.Identification of Vulnerabilities
Vulnerabilities are weaknesses or flaws in an organization's information or information systems that can be exploited by a threat actor. Vulnerabilities can be the result of outdated software, unpatched systems, or misconfigured systems. Identifying vulnerabilities is crucial for preventing cyber attacks. According to a report by the National Cyber Security Alliance, 60% of small businesses close within six months of a cyber attack. This highlights the importance of identifying vulnerabilities and implementing strategies to mitigate those vulnerabilities.

C. Identification of Assets
Assets are the resources that an organization wants to protect from cyber-attacks. Assets can include data, intellectual property, hardware, software, and networks. Identifying assets is essential for prioritizing cybersecurity risks and developing strategies to protect those assets. According to a report by IBM, the average cost of a data breach in 2021 was $4.24 million. This highlights the importance of identifying assets and developing strategies to protect those assets.

3. Risk Analysis
After identifying potential risks, the next step in cybersecurity risk management is analyzing those risks. This involves analyzing the impact of threats and the likelihood of threats.
A. Analysis of the Impact of Threats
The impact of a threat is the potential harm that can be caused to an organization's information or information systems. The impact of a threat can be financial, reputational, or operational. Analyzing the impact of a threat is crucial for prioritizing risks and developing strategies to mitigate those risks. According to a report by the Ponemon Institute, the average cost of a data breach in 2021 was $4.24 million. This highlights the importance of analyzing the impact of threats and developing strategies to mitigate those threats.
B. Analysis of the Likelihood of Threats
The likelihood of a threat is the probability that a threat will occur. Analyzing the likelihood of a threat is essential for prioritizing risks and developing strategies to mitigate those risks. The likelihood of a threat can be influenced by factors such as the organization's security posture, the security posture of third-party vendors, and the threat landscape. According to a report by the Verizon Data Breach Investigations Report, phishing attacks accounted for 36% of data breaches in 2021. This highlights the importance of analyzing the likelihood of threats and developing strategies to mitigate those threats.
4. Risk Identification
After analyzing potential risks, the next step in cybersecurity risk management is developing and implementing strategies to mitigate those risks.
A. Creation of Strategies to Mitigate Risk
Risk mitigation strategies are designed to reduce the impact and likelihood of cyber attacks. These strategies can include implementing security controls such as firewalls, intrusion detection systems, and encryption, as well as developing policies and procedures for incident response and disaster recovery. Risk mitigation strategies should be tailored to the specific risks and assets of the organization. According to a report by the National Institute of Standards and Technology (NIST), implementing security controls can reduce the likelihood of a cyber attack by up to 80%.

B. Implementation of Risk Mitigation Strategies
Implementing risk mitigation strategies involves deploying security controls, training employees on cybersecurity best practices, and regularly testing and updating security measures. The implementation of risk mitigation strategies should be ongoing and should be reviewed regularly to ensure they remain effective. According to a report by Cybersecurity Ventures, cybercrime damages are expected to cost the world $6 trillion annually by 2025. This highlights the importance of implementing risk mitigation strategies to prevent cyber attacks.

5. Risk Monitoring
After implementing risk mitigation strategies, the next step in cybersecurity risk management is monitoring those strategies to ensure they are effective.
A. Monitoring of Security Systems
Monitoring security systems involves monitoring security controls such as firewalls, intrusion detection systems, and anti-virus software to detect and prevent cyber-attacks. Security systems should be monitored continuously to ensure they are functioning correctly and to detect any unusual activity. According to a report by the Ponemon Institute, the average time to identify and contain a data breach was 287 days in 2021. This highlights the importance of monitoring security systems to detect and prevent cyber-attacks.

B. Monitoring of Internal and External Network Activity
Monitoring internal and external network activity involves monitoring network traffic to detect and prevent unauthorized access and unusual activity. Network activity should be monitored continuously to detect and prevent cyber-attacks. According to a report by the Identity Theft Resource Center, there were 1,108 data breaches in the United States in 2021, exposing over 1.6 billion records. This highlights the importance of monitoring network activity to detect and prevent cyber-attacks.
Final thoughts
Managing the risks associated with cybersecurity should be an indispensable part of any company's plan to defend itself from cyberattacks. Best practices for cybersecurity risk management include searching for threats, analyzing their potential impact, creating and implementing countermeasures, and checking in on their performance.
The risk of cyberattacks is constantly present in today's connected world, so businesses need to take preventative measures. Organizations can protect themselves from the potentially disastrous effects of a data breach by adopting the best practices for cybersecurity risk management and thereby lowering the risk of a cyber attack.
If you are looking for a trusted IT partner, VNEXT Global is the ideal choice. With 14+ years of experience, we surely can help you to optimize your business digitalization within a small budget and short time. Currently, we have 400+ IT consultants and developers in Mobile App, Web App, System Development, Blockchain Development and Testing Services. We have provided solutions to 600+ projects in several industries for clients worldwide. We are willing to become a companion on your way to success. Please tell us when is convenient for you to have an online meeting to discuss this further. Have a nice day!